The default installation of RHEL6 installs openssh-server, thus it is a bit strange that this objective is here at any rate.
SSH
You can check this in your box by issuing the following command:
rpm -qa | grep ssh
which in my box results in this:
openssh-server-5.3p1-20.el6.x86_64
openssh-5.3p1-20.el6.x86_64
openssh-clients-5.3p1-20.el6.x86_64
libssh2-1.2.2-7.el6.x86_64
If openssh-server is not installed, you can install it with the following command:
yum install openssh, openssh-clients, openssh-server, libssh2
Once openssh-server is installed, now we need to make sure that we can use to connect to the server, therefore we need to open the firewall, which can be done with this command:
iptables -I INPUT -p tcp --dport ssh -m state --state NEW,RELATED,ESTABLISHED -j ACCEPT
You can save this configuration issuing the following command:
iptables-save > /etc/sysconfig/iptables
VNC
VNC is not installed by default, at least it isn't in my box, and thus needs to be installed:
yum install tigervnc-server
by the way, if you are unsure of what a package is named, you could search yum with
yum whatprovides */vncserver
Make sure that the vnc server is ready to run
chkconfig --list | grep vnc
I get this:
vncserver 0:off 1:off 2:off 3:on 4:off 5:on 6:off
If vncserver is not set to run on runlevel 5, then you should make sure that it does, with the following command:
chkconfig --level 5 vncserver on
Now, you need to add a vnc password to your user, so type and follow the instructions:
vncpasswd
You will need to edit the /etc/sysconfig/vncservers file to add your user, like I've done in my box:
VNCSERVERS="1:auser 2:anotheruser"
VNCSERVERARGS[1]="-geometry 1200x800"
VNCSERVERARGS[2]="-geometry 1024x768"
You can start the server now with: service vncserver start or /etc/init.d/vncserver start, which in my box results in the following output, informing me that there is a Desktop listening for each user.
1:user
New 'RHEL6Blade:1 (user)' desktop is RHEL6Blade:1
Starting applications specified in /home/user/.vnc/xstartup
Log file is /home/user/.vnc/RHEL6Blade:1.log
Starting VNC server: 2:anotheruser
New 'RHEL6Blade:2 (anotheruser)' desktop is RHEL6Blade:2
Starting applications specified in /home/anotheruser/.vnc/xstartup
Log file is /home/anotheruser/.vnc/RHEL6Blade:2.log
This means that you will be able to connect with user user on port 5901 and user anotheruser on port 5902, thus you need to open your firewall accordingly.
iptables -I INPUT -p tcp --dport 5901:5902 -m state --state NEW,RELATED,ESTABLISHED -j ACCEPT
I've had to modify this line in the .vnc/xstartup file:
xterm -geometry 80x24+10+10 -ls -title "$VNCDESKTOP Desktop" & twm
to this line:
xterm -geometry 80x24+10+10 -ls -title "$VNCDESKTOP Desktop" &
#twm &
exec gnome-session &
However, it seems to work OK now, thus I'm not too sure what is going on here, a bit of reading is called for I guess.
Tuesday, 31 May 2011
RHCSA + RHCE Objectives
I intend to go through these exams at some point in the near future and I thought it would be handy to have the objectives for both exams here.
I'll attempt to link newer post to the relevant objective, where appropriate. Almost always, it won't be appropriate and in that case I have made an attempt to link to a page with the relevant information for the objective.
Feel free to suggest a better or alternatively link to ones I have provided.
RHCSA Exam Objectives
Red Hat reserves the right to add, modify and remove objectives. Such changes will be made public in advance through revisions to this document.
RHCSA exam candidates should be able to accomplish the tasks below without assistance. These have been grouped into several categories.
Understand and Use Essential Tools
* Access a shell prompt and issue commands with correct syntax
* Use input-output redirection (>, >>, |, 2>, etc.)
* Use grep and regular expressions to analyze text
* Access remote systems using ssh and VNC
* Log in and switch users in multi-user runlevels
* Archive, compress, unpack and uncompress files using tar, star, gzip, and bzip2
* Create and edit text files
* Create, delete, copy and move files and directories
* Create hard and soft links
* List, set and change standard ugo/rwx permissions
* Locate, read and use system documentation including man, info, and files in /usr/share/doc .
[Note: Red Hat may use applications during the exam that are not included in Red Hat Enterprise Linux for the purpose of evaluating candidate's abilities to meet this objective.]
Operate Running Systems
* Boot, reboot, and shut down a system normally
* Boot systems into different runlevels manually
* Use single-user mode to gain access to a system
* Identify CPU/memory intensive processes, adjust process priority with renice, and kill processes
* Locate and interpret system log files
* Access a virtual machine's console
* Start and stop virtual machines
* Start, stop and check the status of network services
Configure Local Storage
* List, create, delete and set partition type for primary, extended, and logical partitions
* Create and remove physical volumes, assign physical volumes to volume groups, create and delete logical volumes
* Create and configure LUKS-encrypted partitions and logical volumes to prompt for password and mount a decrypted file system at boot
* Configure systems to mount file systems at boot by Universally Unique ID (UUID) or label
* Add new partitions, logical volumes and swap to a system non-destructively
Create and Configure File Systems
* Create, mount, unmount and use ext2, ext3 and ext4 file systems
* Mount, unmount and use LUKS-encrypted file systems
* Mount and unmount CIFS and NFS network file systems
* Configure systems to mount ext4, LUKS-encrypted and network file systems automatically
* Extend existing unencrypted ext4-formatted logical volumes
* Create and configure set-GID directories for collaboration
* Create and manage Access Control Lists (ACLs)
* Diagnose and correct file permission problems
Deploy, Configure and Maintain Systems
* Configure networking and hostname resolution statically or dynamically
* Schedule tasks using cron
* Configure systems to boot into a specific runlevel automatically
* Install Red Hat Enterprise Linux automatically using Kickstart
* Configure a physical machine to host virtual guests
* Install Red Hat Enterprise Linux systems as virtual guests
* Configure systems to launch virtual machines at boot
* Configure network services to start automatically at boot
* Configure a system to run a default configuration HTTP server
* Configure a system to run a default configuration FTP server
* Install and update software packages from Red Hat Network, a remote repository, or from the local filesystem
* Update the kernel package appropriately to ensure a bootable system
* Modify the system bootloader
Manage Users and Groups
* Create, delete, and modify local user accounts
* Change passwords and adjust password aging for local user accounts
* Create, delete and modify local groups and group memberships
* Configure a system to use an existing LDAP directory service for user and group information
Manage Security
* Configure firewall settings using system-config-firewall or iptables
* Set enforcing and permissive modes for SELinux
* List and identify SELinux file and process context
* Restore default file contexts
* Use boolean settings to modify system SELinux settings
* Diagnose and address routine SELinux policy violations
RHCE Exam Objectives
Red Hat reserves the right to add, modify and remove objectives. Such changes will be made public in advance through revisions to this document.
RHCE exam candidates should be able to accomplish the following without assistance. These have been grouped into several categories.
System Configuration and Management
* Route IP traffic and create static routes
* Use iptables to implement packet filtering and configure network address translation (NAT)
* Use /proc/sys and sysctl to modify and set kernel run-time parameters
* Configure system to authenticate using Kerberos
* Build a simple RPM that packages a single file
* Configure a system as an iSCSI initiator that persistently mounts an iSCSI target
* Produce and deliver reports on system utilization (processor, memory, disk, and network)
* Use shell scripting to automate system maintenance tasks
* Configure a system to log to a remote system
* Configure a system to accept logging from a remote system
Network Services
Network services are an important subset of the exam objectives. RHCE candidates should be capable of meeting the following objectives for each of the network services listed below:
* Install the packages needed to provide the service
* Configure SELinux to support the service
* Configure the service to start when the system is booted
* Configure the service for basic operation
* Configure host-based and user-based security for the service
RHCE candidates should also be capable of meeting the following objectives associated with specific services:
HTTP/HTTPS
* Configure a virtual host
* Configure private directories
* Deploy a basic CGI application
* Configure group-managed content
DNS
* Configure a caching-only name server
* Configure a caching-only name server to forward DNS queries
* Note: Candidates are not expected to configure master or slave name servers
FTP
* Configure anonymous-only download
NFS
* Provide network shares to specific clients
* Provide network shares suitable for group collaboration
SMB
* Provide network shares to specific clients
* Provide network shares suitable for group collaboration
SMTP
* Configure a mail transfer agent (MTA) to accept inbound email from other systems
* Configure an MTA to forward (relay) email through a smart host
SSH
* Configure key-based authentication
* Configure additional options described in documentation
NTP
* Synchronize time using other NTP peers
I'll attempt to link newer post to the relevant objective, where appropriate. Almost always, it won't be appropriate and in that case I have made an attempt to link to a page with the relevant information for the objective.
Feel free to suggest a better or alternatively link to ones I have provided.
RHCSA Exam Objectives
Red Hat reserves the right to add, modify and remove objectives. Such changes will be made public in advance through revisions to this document.
RHCSA exam candidates should be able to accomplish the tasks below without assistance. These have been grouped into several categories.
Understand and Use Essential Tools
* Access a shell prompt and issue commands with correct syntax
* Use input-output redirection (>, >>, |, 2>, etc.)
* Use grep and regular expressions to analyze text
* Access remote systems using ssh and VNC
* Log in and switch users in multi-user runlevels
* Archive, compress, unpack and uncompress files using tar, star, gzip, and bzip2
* Create and edit text files
* Create, delete, copy and move files and directories
* Create hard and soft links
* List, set and change standard ugo/rwx permissions
* Locate, read and use system documentation including man, info, and files in /usr/share/doc .
[Note: Red Hat may use applications during the exam that are not included in Red Hat Enterprise Linux for the purpose of evaluating candidate's abilities to meet this objective.]
Operate Running Systems
* Boot, reboot, and shut down a system normally
* Boot systems into different runlevels manually
* Use single-user mode to gain access to a system
* Identify CPU/memory intensive processes, adjust process priority with renice, and kill processes
* Locate and interpret system log files
* Access a virtual machine's console
* Start and stop virtual machines
* Start, stop and check the status of network services
Configure Local Storage
* List, create, delete and set partition type for primary, extended, and logical partitions
* Create and remove physical volumes, assign physical volumes to volume groups, create and delete logical volumes
* Create and configure LUKS-encrypted partitions and logical volumes to prompt for password and mount a decrypted file system at boot
* Configure systems to mount file systems at boot by Universally Unique ID (UUID) or label
* Add new partitions, logical volumes and swap to a system non-destructively
Create and Configure File Systems
* Create, mount, unmount and use ext2, ext3 and ext4 file systems
* Mount, unmount and use LUKS-encrypted file systems
* Mount and unmount CIFS and NFS network file systems
* Configure systems to mount ext4, LUKS-encrypted and network file systems automatically
* Extend existing unencrypted ext4-formatted logical volumes
* Create and configure set-GID directories for collaboration
* Create and manage Access Control Lists (ACLs)
* Diagnose and correct file permission problems
Deploy, Configure and Maintain Systems
* Configure networking and hostname resolution statically or dynamically
* Schedule tasks using cron
* Configure systems to boot into a specific runlevel automatically
* Install Red Hat Enterprise Linux automatically using Kickstart
* Configure a physical machine to host virtual guests
* Install Red Hat Enterprise Linux systems as virtual guests
* Configure systems to launch virtual machines at boot
* Configure network services to start automatically at boot
* Configure a system to run a default configuration HTTP server
* Configure a system to run a default configuration FTP server
* Install and update software packages from Red Hat Network, a remote repository, or from the local filesystem
* Update the kernel package appropriately to ensure a bootable system
* Modify the system bootloader
Manage Users and Groups
* Create, delete, and modify local user accounts
* Change passwords and adjust password aging for local user accounts
* Create, delete and modify local groups and group memberships
* Configure a system to use an existing LDAP directory service for user and group information
Manage Security
* Configure firewall settings using system-config-firewall or iptables
* Set enforcing and permissive modes for SELinux
* List and identify SELinux file and process context
* Restore default file contexts
* Use boolean settings to modify system SELinux settings
* Diagnose and address routine SELinux policy violations
RHCE Exam Objectives
Red Hat reserves the right to add, modify and remove objectives. Such changes will be made public in advance through revisions to this document.
RHCE exam candidates should be able to accomplish the following without assistance. These have been grouped into several categories.
System Configuration and Management
* Route IP traffic and create static routes
* Use iptables to implement packet filtering and configure network address translation (NAT)
* Use /proc/sys and sysctl to modify and set kernel run-time parameters
* Configure system to authenticate using Kerberos
* Build a simple RPM that packages a single file
* Configure a system as an iSCSI initiator that persistently mounts an iSCSI target
* Produce and deliver reports on system utilization (processor, memory, disk, and network)
* Use shell scripting to automate system maintenance tasks
* Configure a system to log to a remote system
* Configure a system to accept logging from a remote system
Network Services
Network services are an important subset of the exam objectives. RHCE candidates should be capable of meeting the following objectives for each of the network services listed below:
* Install the packages needed to provide the service
* Configure SELinux to support the service
* Configure the service to start when the system is booted
* Configure the service for basic operation
* Configure host-based and user-based security for the service
RHCE candidates should also be capable of meeting the following objectives associated with specific services:
HTTP/HTTPS
* Configure a virtual host
* Configure private directories
* Deploy a basic CGI application
* Configure group-managed content
DNS
* Configure a caching-only name server
* Configure a caching-only name server to forward DNS queries
* Note: Candidates are not expected to configure master or slave name servers
FTP
* Configure anonymous-only download
NFS
* Provide network shares to specific clients
* Provide network shares suitable for group collaboration
SMB
* Provide network shares to specific clients
* Provide network shares suitable for group collaboration
SMTP
* Configure a mail transfer agent (MTA) to accept inbound email from other systems
* Configure an MTA to forward (relay) email through a smart host
SSH
* Configure key-based authentication
* Configure additional options described in documentation
NTP
* Synchronize time using other NTP peers
Sunday, 29 May 2011
Testing sending mail with Postfix
Yesterday, I was looking for a simple way of testing my installation of postfix and after a bit of digging I found the following:
telnet 10.168.20.229 25
Trying 10.168.20.229...
Connected to 10.168.20.229.
Escape character is '^]'.
220 RHEL6KSTest1.dev.com ESMTP Postfix
EHLO hostname
250-rh.dev.com
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
MAIL FROM: crazy@dev.com
250 2.1.0 Ok
RCPT TO: loco@dev.com
250 2.1.5 Ok
DATA
354 End data with.
This is a test email
.
250 2.0.0 Ok: queued as B8EF51A4D
quit
You might need to install telnet (yum install telnet)
You can then check with mail:
[root@RHEL6KSTest1 ~]# mail -u loco
Heirloom Mail version 12.4 7/29/08. Type ? for help.
"/var/spool/mail/root": 1 message
> 1 crazy@dev.com Sun May 29 12:16 15/511
&
telnet 10.168.20.229 25
Trying 10.168.20.229...
Connected to 10.168.20.229.
Escape character is '^]'.
220 RHEL6KSTest1.dev.com ESMTP Postfix
EHLO hostname
250-rh.dev.com
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
MAIL FROM: crazy@dev.com
250 2.1.0 Ok
RCPT TO: loco@dev.com
250 2.1.5 Ok
DATA
354 End data with
This is a test email
.
250 2.0.0 Ok: queued as B8EF51A4D
quit
You might need to install telnet (yum install telnet)
You can then check with mail:
[root@RHEL6KSTest1 ~]# mail -u loco
Heirloom Mail version 12.4 7/29/08. Type ? for help.
"/var/spool/mail/root": 1 message
> 1 crazy@dev.com Sun May 29 12:16 15/511
&
Wednesday, 25 May 2011
Microsoft Dynamics CRM 4.0 and the importance of the Internet Guest Account
We are in the middle of System testing for this project and on Monday we hit a really strange issue.
We applied a patch build of Friday afternoon and on Monday morning, testers are reporting different behaviour, some are encountering the issue, some are not. The plot thickens.
I have a look and see that there are some javascript errors in the Homepage.aspx and bar_top.aspx pages in the _root folder, which prevent the home page from loading.
This is the error ( related to the homepage.aspx, but also to the bar_top.aspx page)
Did I mention that we have customized these pages? Well, we have. There is some JavaScript to find which roles each user has, anyway.
I look at the custom code in these pages and sure enough there are some bugs in them. We let the developers know and that should have been the end of it, but we dig a little deeper and it turns out that the bugs in our code are not responsible for the behaviour we are seeing.
Next step the Event Log and CRM trace log. I find this rather useful error in the latter (nothing worth mentioning in the former):
>CrmAuthenticationToken is missing.
Not very helpful, I'm sure you'll agree, but our custom code calls the getauthenticationheader method and I thought this must be the source of our problem. After a bit of a hunt, I managed to locate the vanilla homepage and bar_top pages, copied then, bounced IIS, Async Service restarted but to no avail, the error persists.
I'm out of ideas so Verbose Trace logging here we come. This generates several hundred KB of logging and my heart sinks.
I decide to clear the security log and have another try. This reveals that the internet guest account is locked out and after unlocking it we are up and running again.
P.S.
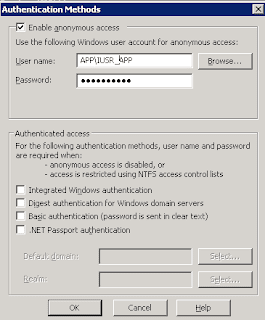
If you are wondering why the internet guest account is locked out, the answer is I don't know for sure. I know that we were setting a web service to always use the service account and thus we set it in Anonymous Access, like this:
At some point, we must've typed the password for the service account, but left the internet guest account and after that it was only a matter of time for the behaviour to start occurring.
.
We applied a patch build of Friday afternoon and on Monday morning, testers are reporting different behaviour, some are encountering the issue, some are not. The plot thickens.
I have a look and see that there are some javascript errors in the Homepage.aspx and bar_top.aspx pages in the _root folder, which prevent the home page from loading.
This is the error ( related to the homepage.aspx, but also to the bar_top.aspx page)
 | |
| Note that our Custom Code means that the line is completely different to yours |
Did I mention that we have customized these pages? Well, we have. There is some JavaScript to find which roles each user has, anyway.
I look at the custom code in these pages and sure enough there are some bugs in them. We let the developers know and that should have been the end of it, but we dig a little deeper and it turns out that the bugs in our code are not responsible for the behaviour we are seeing.
Next step the Event Log and CRM trace log. I find this rather useful error in the latter (nothing worth mentioning in the former):
>CrmAuthenticationToken is missing.
Not very helpful, I'm sure you'll agree, but our custom code calls the getauthenticationheader method and I thought this must be the source of our problem. After a bit of a hunt, I managed to locate the vanilla homepage and bar_top pages, copied then, bounced IIS, Async Service restarted but to no avail, the error persists.
I'm out of ideas so Verbose Trace logging here we come. This generates several hundred KB of logging and my heart sinks.
I decide to clear the security log and have another try. This reveals that the internet guest account is locked out and after unlocking it we are up and running again.
P.S.
If you are wondering why the internet guest account is locked out, the answer is I don't know for sure. I know that we were setting a web service to always use the service account and thus we set it in Anonymous Access, like this:
.
Subscribe to:
Comments (Atom)