So thus far, we have a CA and a secure web site, so the missing piece in the puzzle is the client certificate, thus let's dive right in, except that: It turns out that in order to create a client certificates the CA website must be running securely.
You can use the procedure described in my previous post to generate a new server certificate and then you can install it as follows: Start|Run|inetmgr
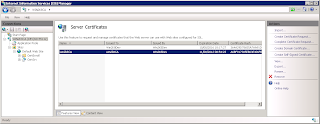
Although the GUI has changed, the procedure is the pretty much the same as described in my previous post, for both the request and then the completion of the request. Once completed, you'll have a new server certificate installed:
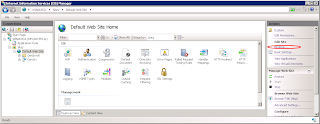
Now go the default website on IIS Manager and add a new Binding:
Note that I have selected the same certificate that I created before. We can now navigate to the CA website using ssl.
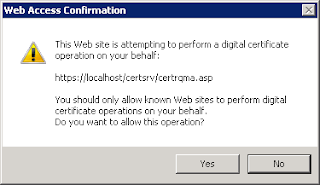
Note, that if you use https://localhost/certsrv you'll see a warning unless you specifically created the certificate for localhost, but if you don't you'll need to change you trusted sites settings so that activex controls can run.
We can now request a client certificate.
You'll get the following prompt, just press yes to continue:
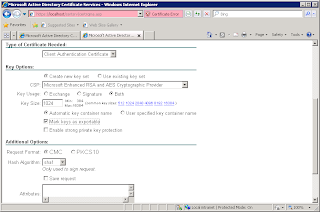
Fill in the identity information, not shown, and then make sure that you tick mark keys as exportable and press submit.
You'll get the usual message about the request being pending, see my previous post for details on how to deal with this.
Once you have issued the certificate you'll need to install it, from the main CA webpage, go to View the Status of Pending Certificate Request:
In my case, it's failing to determine the revocation status, which means that I probably messed up somewhere. Irritation. See this post for a solution to this issue










No comments:
Post a Comment