Following on from Sunday's post on how to set up phpMyAdmin on CentOS 6.2, I thought it would be a good idea to set up phpMyAdmin as a secure website (HTTPS), rather than in clear-text (HTTP). This will ensure that all traffic between the web browser and phpMyAdmin is encrypted.
In a previous post I set up a Certification Authority so I will be using this CA to generate the necessary certificates, but don't worry if you don't have one, you can use makecert or OpenSSL to generate a self signed certificate.
All that is needed is a server and CA certificate, if you've followed my previous post on phpMyAdmin, you can go directly to step 7. Thus armed with a pkcs#12 server certificate (phpMyAdmin.pfx) and a CA certificate (win2kca.cer) we can start:
- Set SELinux to allow Apache to bind to a non-default port:
setsebool -P allow_ypbind 1
- Download EPEL Release to enable usage of EPEL Repository:
wget http://download.fedora.redhat.com/pub/epel/6/i386/epel-release-6-5.noarch.rpm
- Install EPEL Release package:
yum install epel-release-6-5.noarch.rpm -y
- Install phpMyAdmin:
yum install phpmyadmin -y
- Create new directory to host the phpMyAdmin website:
mkdir /var/www/phpMyAdmin
- Copy phpMyAdmin installation to the directory created in the previous step:
cp -r /usr/share/phpMyAdmin/. /var/www/phpMyAdmin
- Extract public and private key from server certificate:
openssl pkcs12 -in phpMyAdmin.pfx -out phpMyAdmin.key -nodes -nocerts
openssl pkcs12 -in phpMyAdmin.pfx -out phpMyAdmin.crt -nodes -nokeys - Restrict permissions on key file:
chmod 400 phpMyAdmin.key
- Create certificate and key directories and move certificates and keys to them:
mkdir /etc/httpd/conf.d/certs
mkdir /etc/httpd/conf.d/keys
mv phpMyAdmin.crt /etc/httpd/conf.d/certs
mv phpMyAdmin.key /etc/httpd/conf.d/keys
cp win2k8ca.cer /etc/httpd/conf.d/certs - Set SELinux to permissive, this is to prevent issues with SELinux preventing Apache from working properly:
setenforce 0
- Edit Apache's SSL configuration file (/etc/httpd/conf.d/ssl.conf). I have changed the port to 7777 and prevented LOW ciphers from being accepted. The rest is simply providing the location of the certificates. Only listing relevant parts of ssl.conf:
Listen 7777
<VirtualHost _default_:7777>
# SSL Cipher Suite:
SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM
# Server Certificate:
SSLCertificateFile /etc/httpd/conf.d/certs/phpMyAdmin.crt
# Server Private Key:
SSLCertificateKeyFile /etc/httpd/conf.d/certs/phpMyAdmin.key
# Server Certificate Chain:
SSLCertificateChainFile /etc/httpd/conf.d/certs/win2k8ca.cer
# Certificate Authority (CA):
SSLCACertificateFile /etc/httpd/conf.d/certs/win2k8ca.cer
</VirtualHost>- You can check that the apache configuration file is correct by using:
apachectl -t
- You can check that the apache configuration file is correct by using:
- Restart Apache:
apachectl -k restart or service httpd restart
- Open firewall for port 7777 and save IPTables configuration:
iptables -I INPUT -p tcp --dport 7777 -j ACCEPT; service iptables save
- You can now navigate to https://phpmyadmin.dev.com:7777/setup (If you are using Chrome, you will see this screen first. Other browsers will show similar screens). Note that you'll need a entry on your hosts file that points phpmyadmin.dev.com to the IP address of the Server: Click Procceed anyway. You are seeing this because your CA is not trusted by Chrome. Although it would seem that the connection is not encrypted, the icon is misleading, it just means that it is not trusted. See below for confirmation:
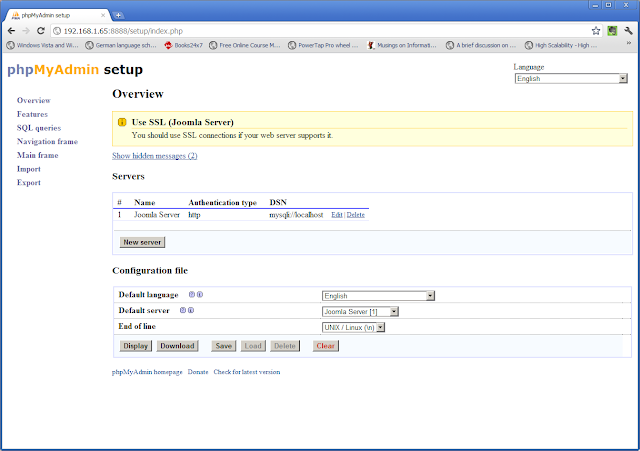
- Because I'm lazy, I'm going to reuse the screenshots and text from my previous phpMyAdmin post, so .. Click New Server. I only changed the name and compression, accepted defaults for everything else:
- Go To Authentication Tab. See this link for an overview of the authentication types:
- Click Save, which will bring you to the screen below:
- Download the configuration file (config.inc.php) and copy it to /var/www/phpMyAdmin.
- You can now start using phpMyAdmin on https://phpmyadmin.dev.com:7777:
- All that remains is to renable SELinux and deal with the policy violations:
cat /var/log/audit/audit.log | grep denied > ssl
audit2allow -M apachessl -i ssl
semodule -i apachessl.pp
setenforce 1
In theory, the setup script should be able to generate the configuration file for you, but I've not been able to get it to work. Instructions can be found here if you are interested.
I haven't thoroughly tested this setup so it is possible, as always, that there could be SELinux issues. All I can suggest is that, if you have some inexplicable issue, have a look at the SELinux log (/var/log/audit/audit.log).






how to cancel a norton subscription
ReplyDelete