On part 1, I described how to install and configure ADFS on a Windows 2012 R2 server and in this post I will describe how to configure Ms Dynamics CRM 2013 to use claim based authentication.
Pre-Requisite:
- A wildcard certificate with private key installed.
The first step is to ensure that the Ms Dynamics CRM 2013 website is configured to use HTTPS, so from the IIS Manager (Windows Key + R -> inetmgr):
Add New Binding
Note that IIS will display the certificate friendly name here, you can always click view to ensure that you have the correct certificate here.
Click Ok and then Click Close.
Ms Dynamics CRM 2013 should now be available on HTTPS :)
Now we need to ensure that the service account for the CRM website, i.e. the account that run CRMAppPool, has access to the private key of the wildcard certificate, so from a certificate console (Windows Key + R -> mmc -> ctrl + M -> Certificates -> Computer Account):
Note how because I'm using Network Service to run the CRMAppPool, that is the account that needs to be able to read the private key.
The next step is to configure Ms Dynamics CRM 2013 for Claim based authentication.
First we need to ensure that the binding type is set to HTTPS.
From the Deployment Manager.
Set Binding Type to HTTPS (There is no need to have the port number)
Make sure you that you click Apply.
Click on Configure Claim Based Authentication and follow the wizard.
It is possible to copy the URL for the relying party by opening the log file and scrolling down to the bottom of the file.
From the ADFS server, start the ADFS Management Console (Server Manager -> Tools -> AD FS Management). We need to ensure that Forms Authentication will be allowed from the internal network. Click on Authentication Policies, then on Edit.
Tick Forms Authentication and click Ok.
A claim rule is needed to obtain the UPN from the Active Directory domain, so from Claim Provider Trust, select Active Directory and click on Edit Claim Rules..
Click Add Rule
We are now ready to add a relying party trust, so on the Relying Party Trust menu, click on Add Relying Party Trust.
Note how this is the URL the Claims Based authentication wizard tells us to use for configuring a relying trust, it's https://<FQDN>/FederationMetadata/2007-06/FederationMetadata.xml.
Once the wizard completes (just click Next until you get to the end), it is necessary to add three Issuance Transform Rules.
A Pass Through Rule for UPN:
A Pass Through Rule for Primary SID:
A Transform Rule for Windows Account Name:
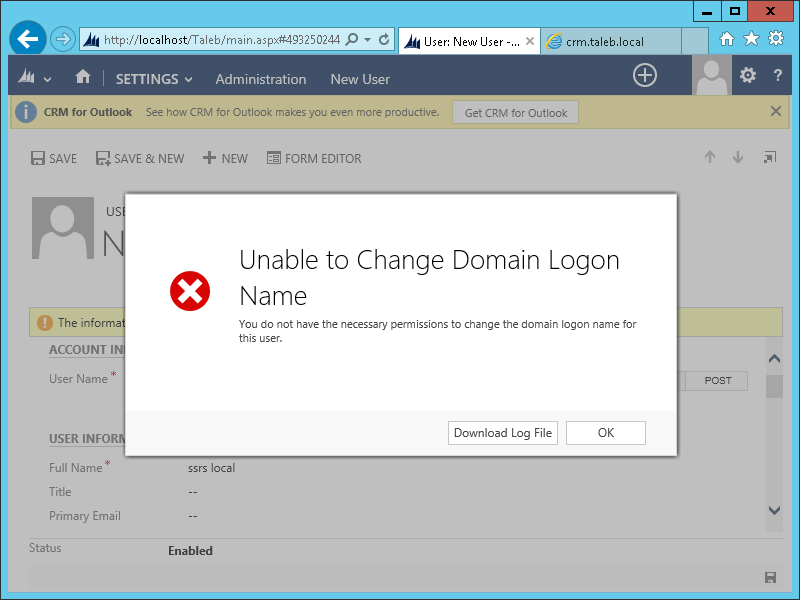
At this point I hit another snag. I tried to add a new user with UPN format, e.g. sts@taleb.local and I had this error:
The solution was to turn Auto Group Management Off, which is done via a registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSCRM\AutoGroupManagementOff
Default value is 0, i.e. Auto Group Management is On
It can be turned off by setting it to 1.
Having done this, I was able to add a new user in UPN format and successfully sign in:




























No comments:
Post a Comment