In this post, I showed how it can be used to test cipher levels. Today I'll show how it can be used as a simple SSL server to test, .. an SSL client, I guess. Since I already have a CA, I'm going to use that CA, which means that I generate a certificate request using the following command:
openssl req -new -newkey rsa:1024 -nodes -subj '/CN=RHEL6Blade/O=dev.com/C=UK/ST=Yorkshire/L=Here' -keyout key.pem -out myreq.pemI submit the certificate request to said CA and come back to my linux box with two files:
- certificate file. Ensure that this was exported as a Base64 certificate - redhat.cer
- pkcs7 file i.e. certificate chain - redhat.p7b
cat key.pem redhat.cer > key-cert.pemI then convert the pkcs7 chain into a pem file with the following command:
openssl pkcs7 -in redhat.p7b -noout -out test.pemFinally, I can run the SSL server with the following command:
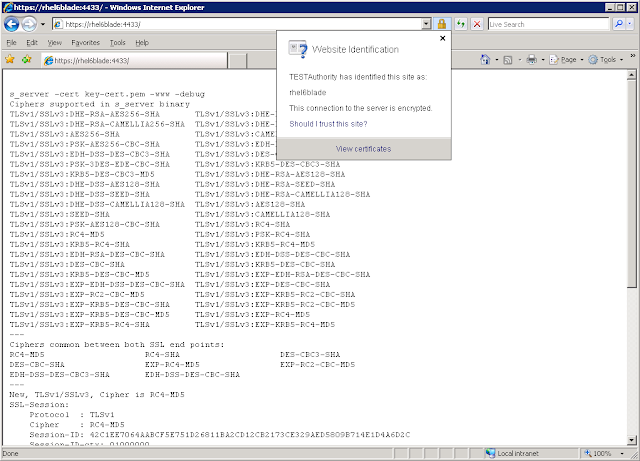
openssl s_server -cert key-cert.pem -www -debug -CAfile test.pemFrom a windows machine running IE 7, using the hostname only:
If I use the fully qualified domain name, I get this error as the url and the certificate name don't match:
If I omit the -CAfile command from the server, i.e:
openssl s_server -cert key-cert.pem -www -debugI get the same error even if I use the hostname. This is because the CA is not trusted (if the CA is trusted then there is no need to add the -CAfile modifier):


No comments:
Post a Comment